- KDDI HOME
 Corporate Information
Corporate Information  About KDDI
About KDDI  Released Information
Released Information 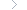 Security Portal
Security Portal 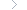 Initiatives for Delivering Safe and Secure Services
Initiatives for Delivering Safe and Secure Services
Initiatives for Delivering Safe and Secure Services


Enhancing Group-wide Information Security
- Measures against cyber attacks
- Measures against breaches of personal information
KDDI's information security management systems have been ISO/IEC 27001-certified [1] throughout the group since 2009. For group companies, KDDI established the KDDI Group
Information Security Common Requirements in 2011 and extended stricter KDDI standards to all group companies from 2017. By promoting the enhancement of security levels throughout the KDDI Group with such establishments and periodically auditing the security statuses of group companies, KDDI continuously works to reinforce information security governance throughout the group. In February 2018, the KDDI Group founded KDDI Digital Security Inc., where security engineers with specialized training combat cyber attacks.
KDDI's ISMS certification
| Registered No. | Organization | Initial registration date |
|---|---|---|
| IS-95253 | KDDI Corporation [2] | June 7,2005 |
Initiatives for Reducing Information Security Risks
- Measures against cyber attacks
- Measures against breaches of personal information
Managing information assets according to importance
At KDDI, we categorize information assets as per the internal information security regulations and have specified the handling of information assets according to their level of importance. Proper information assets management is achieved by applying security measures corresponding to the categorization. For example, customer information can only be handled on terminals to which access is blocked from the Internet. Persons who can access information assets are limited by means of strict permission management. Information assets classified as important information are subject to strong encryption so as to protect them from any external third-party access.
By taking appropriate security measures according to the level of importance of individual information assets, KDDI executes thoroughgoing information asset management.
Information security training for all employees
KDDI provides information security training for all employees and officers by means of e-learning. The training resources are updated every year to reflect the latest threat trends, including case studies of cyber attacks in Japan and abroad and tactics used in attacks targeting employees. Such efforts are conducted to improve the employees' skills and awareness for information security.
In addition to the above, new employee training, new line manager training, and other level-specific training programs are provided amongst the variety of information security training available at KDDI for preventing information security incidents.
Security Check and Vulnerability Diagnosis
- Measures against cyber attacks
As security regulations, KDDI established standards for security measures that business-critical systems should follow and reviews the compliance with these regulations.
These security regulations provide concrete security requirements, along with their interpretations, for systems used by the KDDI Group for planning, development, and operation. These requirements cover physical hardware installation locations, connecting with external networks, software versions, authentication and access control methods, logging, and recordkeeping.
By stringently conducting reviews during the transitional phase from system planning to development, KDDI achieves "security by design" that embodies security measures from the planning and design phase.
Also, in a system's application phase, KDDI runs a network vulnerability diagnosis that detects issues that are present in servers and network.
For network vulnerability diagnosis, KDDI uses a dedicated diagnostic tool with a signature database that accumulates various software vulnerability information to check for possible security issues that may be present in the target server or network device.
The issues identified are classified into different levels based on risks in order to make necessary corrections such as application of security patches and revision of settings.
Such are examples of KDDI's endeavors to ensure system security at each phase of planning, development, and application, in order to deliver safe and secure services.
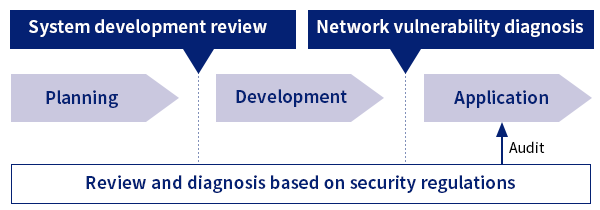
Flow of security check and vulnerability diagnosis
Security Monitoring
- Measures against cyber attacks
KDDI comprehensively monitors its networks nationwide centering around the Security Operation Center (SOC).
In the case of a large-scale network failure, control is centralized at the SOC in order to give instructions internally and externally on recovery response and information sharing. At the SOC, security engineers with specialized training are on duty round-the clock for surveillance of unauthorized access, tampering, targeted attacks, and other cyber-attack threats. The security engineers monitor and analyze logs output from security monitoring devices to detect any signs of attack from the massive volume of data. Upon the onset of a destructive incident such as unauthorized access and tampering, security engineers detect such occurrences in real-time, and if necessary, quickly inform CSIRT and other relevant internal organizations and give instructions.

KDDI SOC (Security Operation Center)
CSIRT Efforts
- Measures against cyber attacks
As a dedicated organization that responds to security incidents, KDDI has set up a computer security incident response team (CSIRT).
CSIRT coordinates with the KDDI Digital Security, a KDDI group company, to receive information on incidents and work on incident handling, response support, and review of recurrence prevention. KDDI's CSIRT is also a member of the Nippon CSIRT Association and coordinates with other CSIRTs in Japan and abroad to share information on trends and measures.
Cyber attacks are getting more advanced day by day. KDDI is stepping up the collection of vulnerability and attack information, analysis of information, and further automation and sophistication of cyber attack responses in order to combat new threats.
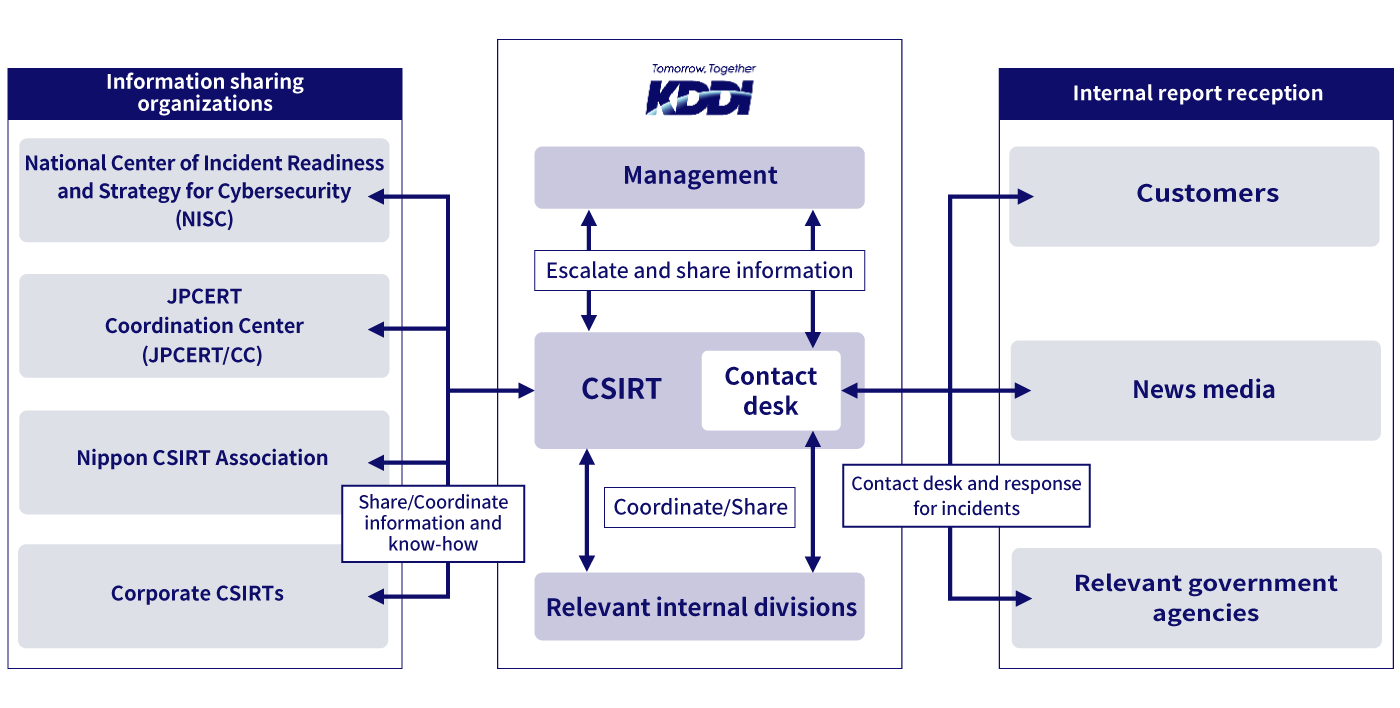
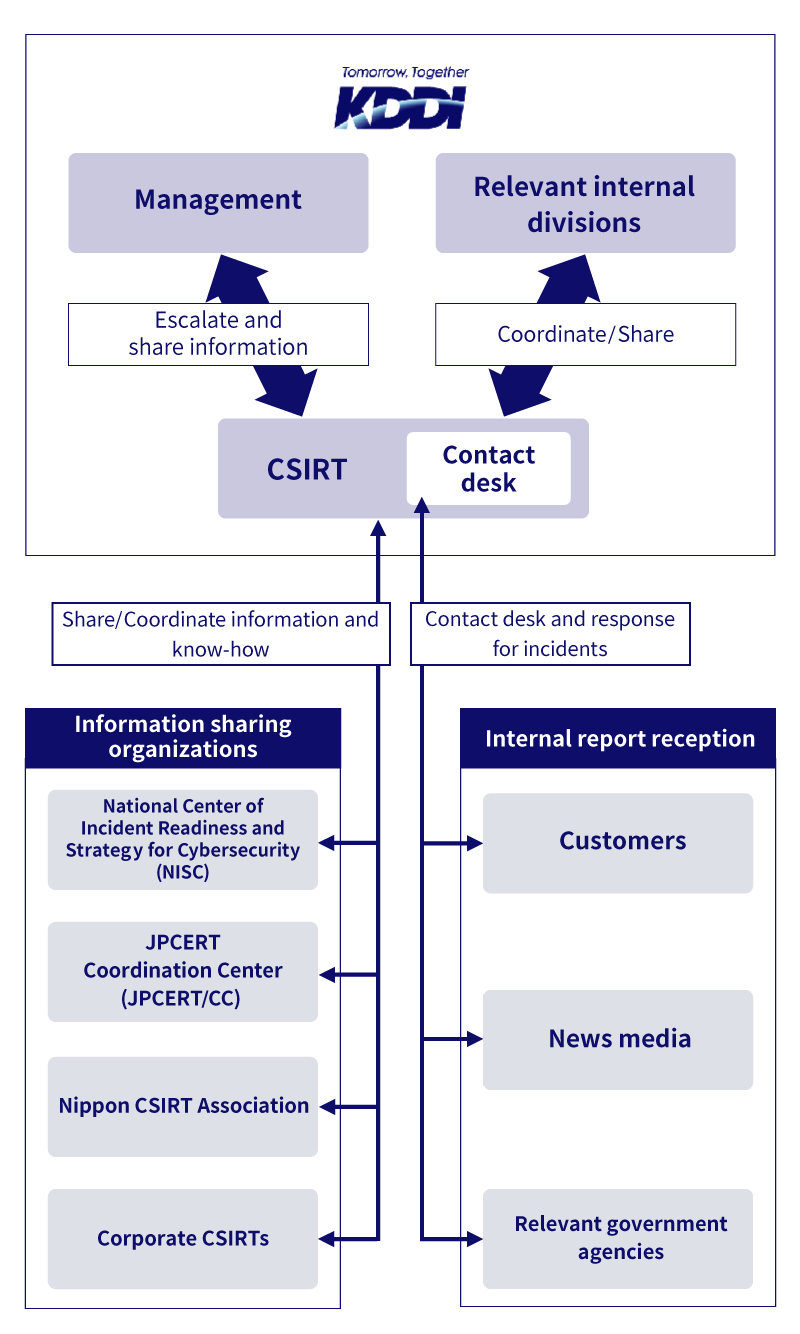
Organizational chart of collaborations with information-sharing organizations and external reporting organizations
Human Resource Development
- Measures against cyber attacks
At KDDI, we define security specialist role models for the purpose of clarifying their career path.
KDDI promotes the acquisition of a wide range of knowledge and deepening of specialization in addition to personnel exchange with external organizations and acquisition of specialized qualifications.
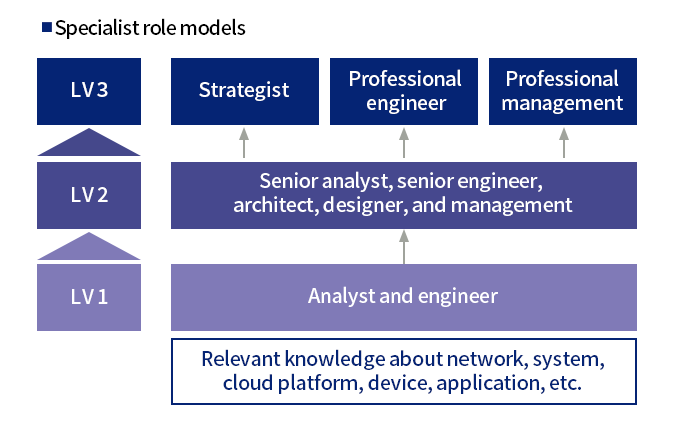
Promoting R&D for Information Security
- Measures against cyber attacks
- Measures against breaches of personal information
Setting the world record at a decoding competition
To contribute to the establishment of secure information communications systems, KDDI promotes research and development to accelerate the decoding algorithm and achieve higher-speed, safer next-generation public key cryptography.
Public key cryptography, a platform technology that supports the safety and security of the Internet and information communications systems, is used nowadays in commodities such as online shopping and IC cards. However, the recent emergence of practical quantum computers has enabled rapid decoding computation, and now we need a public key encryption system that ensures security for quantum computers as well. When using code-based encryption as next-generation public key, it is important to know the bounds on size of codes in order to determine a safe list size.
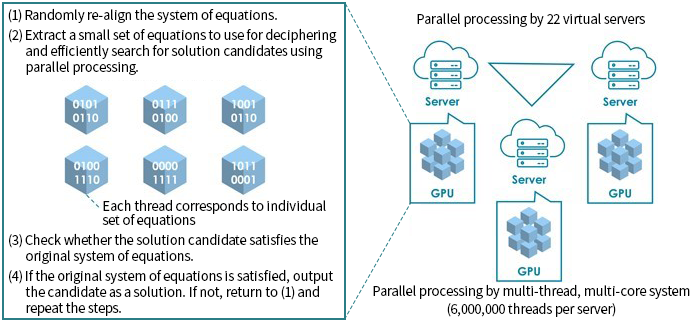
KDDI became the first in the world to solve the Syndrome Decoding problem in the lengths 540 and 550 in the "Challenges for code-based problems" in February 2022.
KDDI also successfully accelerated the decoding process by approximately 226 times through improving the decoding algorithm and optimizing it for a parallel multi-thread environment.
SSIRT Efforts
- Measures against unauthorized use of service
In the past few years, there has been a rapid increase in phishing frauds that guide people to a fake website via e-mail or SMS and steal customers' authentication information. As a dedicated organization that responds to such unauthorized use, KDDI has set up KDDI-SSIRT, a service security incident readiness & response team, to strengthen measures against such acts.
In addition to taking measures to disseminate information on phishing to customers and tackling conventional e-mail scams, KDDI-SSIRT detects fake websites and coordinates with related organizations to eliminate damage caused by malicious websites.
As another security initiative, KDDI-SSIRT also has a round-the-clock surveillance system to identify any unauthorized logins that take over authorized user accounts.
In the review process for new services, KDDI has inserted a new process where specialists audit the service from an anti-unauthorized use perspective as part of the check mechanism to prevent issues in authentication for services.
Phishing tactics are getting shrewder and more sophisticated, to which KDDI will continuously bolster proactive security measures for our services while combating new threats.