- KDDI HOME
 Corporate Information
Corporate Information  Sustainability
Sustainability Cyber Security and Privacy Protection
Cyber Security and Privacy Protection
Cyber Security and Privacy Protection
KDDI's Approach
With the increasing prevalence of smartphones and the rapid progress of technologies such as big data and AI in recent years, new services that make use of various kinds of personal information are being considered.
At the same time, however, these changes have also highlighted many issues surrounding privacy, and governments are reviewing their laws and regulations.
To ensure that it uses personal data while protecting privacy, KDDI has published its privacy policy and its handling of personal information, including types of information to collect, purpose of use and the requirement of a customer's consent, and thus completely protects such personal information based on a zero-tolerance policy. In addition, in January 2020 we set up "Privacy Portal" to provide clear explanation about KDDI's use of customers' information, ensuring the transparency while deepening customers' understanding. In addition, the Privacy Portal was renewed in October 2021, and we are continuously working to provide information and improve its content.
We also need to protect our communication infrastructure from cyberterrorism that causes a failure in the system through unauthorized use of communication infrastructure. KDDI has implemented appropriate defensive measures against external attacks, including 24/7 monitoring by specialists to detect any such attacks. These efforts are aimed at gaining the trust of our customers and stakeholders as a telecommunications carrier responsible for critical lifelines.
Moreover, we have established an internal body dedicated to this purpose, have a third party assess our handling of the information, have adopted a privacy impact assessment (PIA) conducted before a service is introduced, and take other actions in order to further ensure that we properly handle customer information.
Information Security Management Framework
To ensure a unified approach to the security of information assets across the group as a whole, we have established the Information Security Committee chaired by the Director. The committee comprises the management level, along with the general managers of sales, technology and corporate divisions.
Under this framework, we accurately grasp the status of information security management and promptly implement measures to enhance the information security throughout the group.
KDDI also acknowledges that proper information management is a key issue for our business. To ensure information security, we have established the Security Policy that specifies our basic policies on information security, covering information security management framework, the implementation of information security measures, and internal rules about information security, among others.
Information Security Management Framework
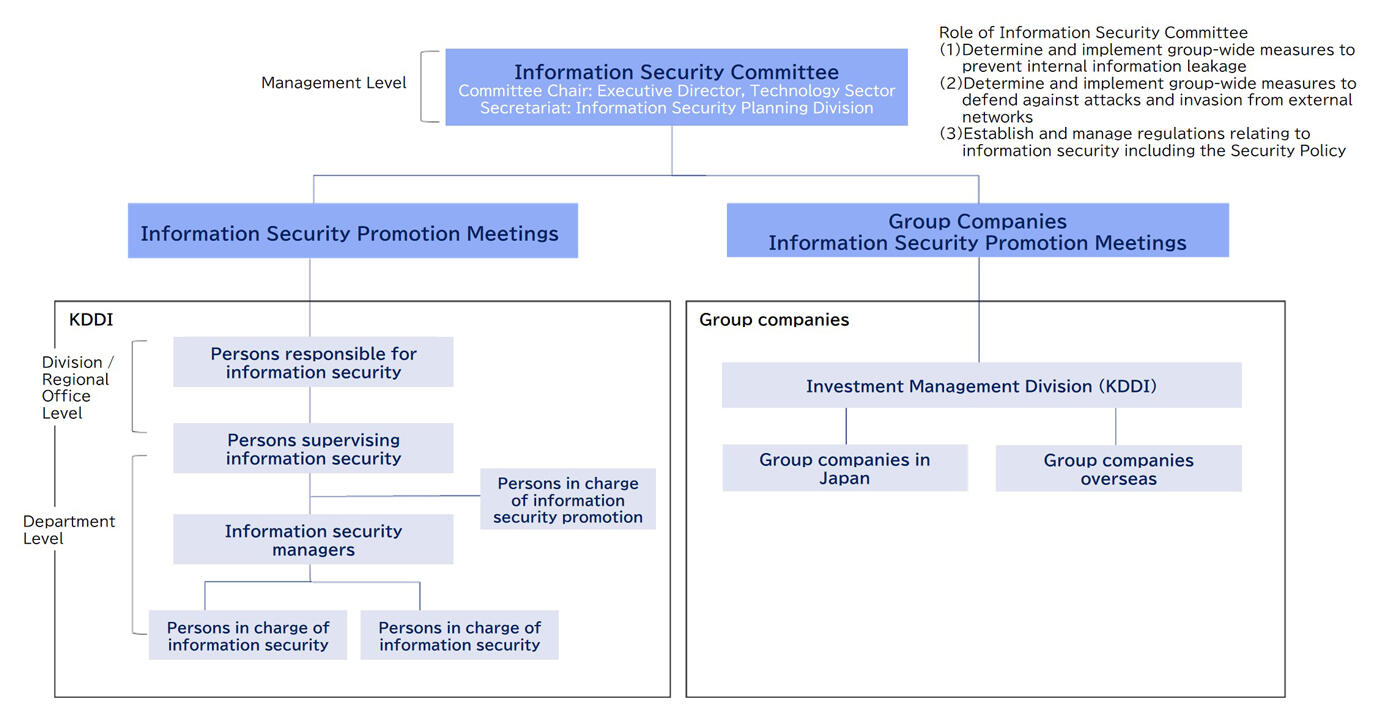
Strengthening Information Security throughout the Company
All KDDI Group companies have been ISMS 27001 [1] certified since 2009. For our group companies, the KDDI Group Information Security Standards were introduced in fiscal 2011. In fiscal 2017, we revised the standards and extended them to apply to all group companies. Augmenting the improvement in the security level of KDDI Group companies resulting from this change, we regularly audit the security level of group companies in an ongoing effort to strengthen the information security governance of the KDDI Group as a whole. Also, KDDI Digital Security Inc. was founded in February 2018, and the company's specially trained security engineers now respond to cyberattacks.
- [1]ISMS certification (ISO/IEC 27001: 2013) A third-party conformity assessment scheme for information security. It was established with the goal of contributing to widespread improvements in information security and encouraging companies to target levels of information security that can be trusted around the world.
ISMS Certification KDDI Acquired
| Registration number | Organization | Initial registration |
|---|---|---|
| IS 95253 | KDDI Corporation [2] | June 7, 2005 |
- [2]Includes corporate, technology and sales and customer support divisions, as well as KDDI Kyosaikai (now KDDI Group Welfare Association), KDDI Health Insurance Union, KDDI Pension Fund, KDDI MATOMETE OFFICE CORPORATION, and Japan Telecommunication Engineering Service Co., Ltd., KDDI Challenged Corporation
Basic Principles concerning the Handling and Use of Personal Data
We have implemented internal rules for the handling of customers' personal data and use of big data in line with the Act on the Protection of Personal Information and other related laws and regulations. We obtain, manage and use such data in accordance with our terms of use for each service and privacy policy.
Data about our subscribers are vital for us. We use the data to help improve customer experience and achieve continuous development of society. We ensure responsible use of data through corporate actions in order to gain customers' understanding. These actions include providing a detailed explanation as to how the data will be used, and processing the data in such a way that the individual will not be identified.
Use of Artificial Intelligence (AI)
In order to further enhance the value of the customer experience and contribute to the sustainable development of society through the use of artificial intelligence (AI), KDDI, formulated the "AI R&D and Utilization Principles for KDDI Group" on August 30, 2021, as part of "KDDI Accelerate 5.0."
Furthermore, to realize AI service development based on these principles, we are promoting the establishment of guidelines and assessment activities. The KDDI Group is advancing awareness campaigns for these principles while also promoting the use of AI in internal business operations, including generative AI. We will utilize the insights gained from these activities to realize AI research and development and the provision of safe and secure AI services to our customers.
Efforts to Reduce Information Security Risks
Management of Information Assets According to Importance
KDDI classifies information assets based on internal information security rules, defines how to handle information assets according to their level of importance, and applies security measures to achieve appropriate information asset management. For example, customer information should only be handled on terminals that are blocked from accessing the Internet, and only limited persons are permitted to access such information assets through strict authorization controls, etc. In addition, information assets classified as critical information are protected by strong encryption so that they cannot be viewed by third parties outside the company. KDDI implements these appropriate security measures in accordance with the importance of information assets to achieve thorough management of such assets.
Information Security Management and Measures
Security Audit and Vulnerability Scanning
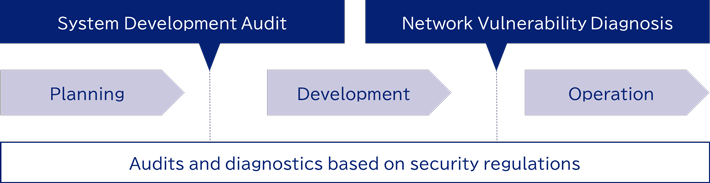
KDDI has a cybersecurity policy prescribing the standards for cyber security measures that our business information system should take, and conducts reviews to see if the policy is followed.
This security rules specify the detailed security requirements, interpretations, and guidelines necessary for the planning, development, and operation of systems within the KDDI Group. It covers aspects such as the physical location of servers and network equipment, connections with external networks, software versions, authentication and access control methods, and the collection and retention of logs.
By rigorously conducting this review during the transition phase from system planning to development, we are ensuring security.
In the phase of system operation, we conduct network vulnerability scanning to identify problems in the servers and networks. Network vulnerability scanning uses a dedicated diagnostic device, in which data on vulnerabilities of various software are saved as a signature database, to identify security issues in the scanned servers and network devices.
The issues that have been found were classified into risk-based levels so that corrective actions are taken, such as applying patches and changing settings.
By taking these actions to ensure information system security in the stages of planning, development, and operation, we offer safe and secure services.
Process of the Security Audit and Vulnerability Scanning
Security Monitoring
KDDI conducts integrated monitoring of nationwide telecommunications facilities system and, in the event of a large-scale failure, coordinates with each location to provide overall control, recovery instructions, and information dissemination. In the event of cyberattacks, we have established a system that allows us to respond quickly by coordinating this integrated monitoring structure with security monitoring. In security monitoring, to protect telecommunications facilities from the threat of cyberattacks, such as unauthorized access, tampering, and targeted attacks, professionally trained security engineers conduct monitoring 24 hours a day, 365 days a year. They monitor and analyze logs generated by security monitoring equipment to identify signs of attacks within a vast amount of log data. Dangerous incidents such as unauthorized access and tampering are detected in real time and KDDI-CSIRT and related divisions within the company work together and cooperate to respond promptly.
Security Monitoring in the SOC (Security Operations Center)

Initiatives by the CSIRT
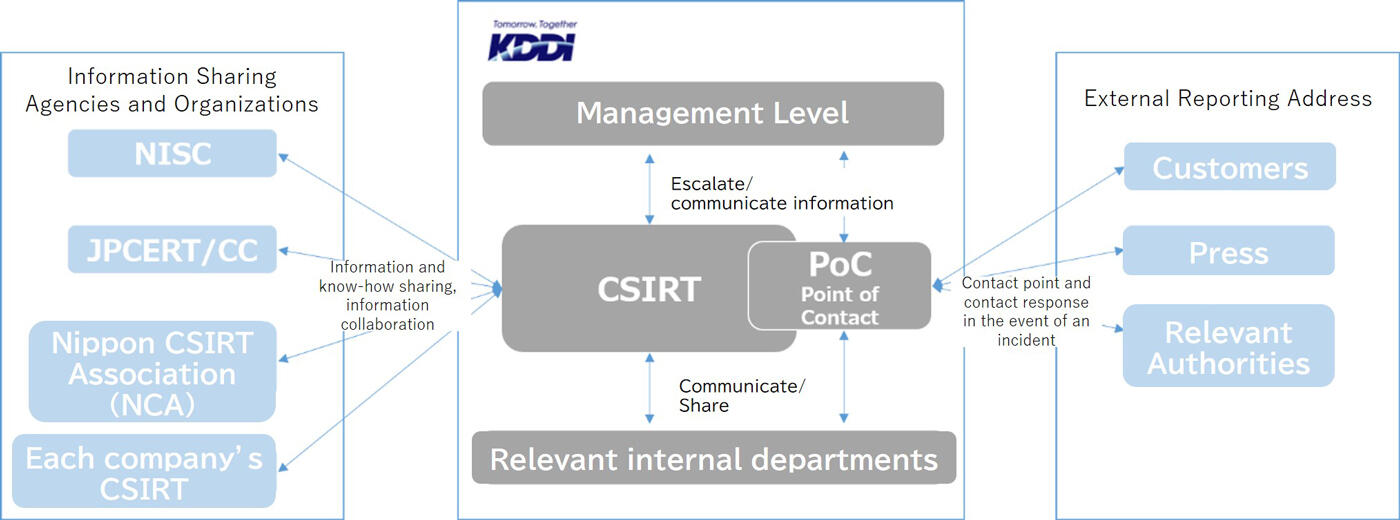
KDDI has the KDDI Computer Security Incident Response Team (KDDICSIRT) as a body dedicated to handling cyber security incidents. The CSIRT works with KDDI Digital Security Inc., KDDI's Group company, to receive incident information, handle the incident response, provide support for the response, and explore recurrence prevention measures, among others. Being a member of the Forum of Incident Response and Security Teams (FIRST) and the Nippon CSIRT Association, the KDDI-CSIRT cooperates with CSIRTs in Japan and overseas to share information about trends and approaches.
In the event of an information security incident, such as information leakage, we will work in collaboration with relevant internal divisions and others as members of the Incident Response Committee, which is established under the Information Security Committee.
Given that cyber-attacks have become increasingly sophisticated, we continually take measures against new threats by collecting more information about vulnerabilities and attacks, analyzing information more thoroughly, and automating and advancing courses of action to handle cyber-attacks.
Process of Cooperation with Information Sharing Agencies and External Reporting Contact
Initiatives by the SSIRT
Over the past few years, there has been a sharp increase in the number of phishing scams that use email or SMS to lure customers to fake websites and steal their credentials in order to commit fraud. KDDI has established the KDDI-SSIRT (Service Security Incident Readiness & response Team) as a specialized organization to deal with this kind of unauthorized use and is working to strengthen countermeasures.
In addition to sending out information to customers about phishing scams and taking conventional anti-spam measures, we are working to prevent damage due to fake websites by detecting the occurrence of fake websites and cooperating with relevant organizations.
Furthermore, we have established a system that conducts 24/7 monitoring for unauthorized login attempts to take over the accounts of authorized users, and we are working to strengthen our countermeasures.
We have also introduced a process in which experts audit new services from the viewpoint of measures against unauthorized use, and have established a checking system to prevent inadequacies in authentication and other aspects of the service.
Since phishing scams are becoming increasingly sophisticated on a daily basis, we will continuously promote proactive security enhancements for each of our services, as well as work on countermeasures against new threats.
Human Resource Development
At KDDI, we have established a security human resource development program and are committed to systematic security human resource development to protect customer data and the services we provide from cyberattacks. In this program, we prioritize employees' growth and career development and actively encourage the acquisition of the national certification "Registered Information Security Specialist (Cybersecurity Specialist)" operated by the Information-technology Promotion Agency (IPA). We provide support for certification preparation, including specialized training and learning assistance. As of April 2023, the number of certified individuals within the KDDI Group is approximately 270, making it one of the largest in the country.
Human resource development is an essential initiative aimed at enhancing employee awareness and nurturing their personal growth. The goal is to significantly enhance KDDI's expertise and technical capabilities through an increase in certified individuals.
Number of Registered Information Security Specialists: 274
- *Based on the IPA public directory, those registered with the employer's name "KDDI Corporation" are extracted.
- *Aggregate for April 2023
Additionally, we conduct stratified e-learning and group-based information security training for a target audience of 11,000 employees, continuously working on improving the security awareness and skills of our employees.
Examples of Information Security Training
| Content | Target | Implementation method |
|---|---|---|
| Security training for new employees | New employees | Group-based training |
| Basic security training | All employees | e-learning |
| Security training for line managers | Line managers | e-learning/Group-based training |
Enhancement of Security Monitoring
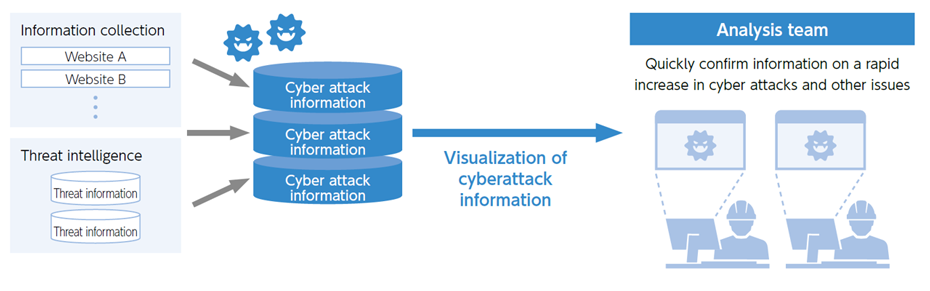
To protect the information entrusted to us by our customers and handled in our services, we are constantly monitoring against cyber-attacks. In March 2023, we completed the construction of a platform that collects information on cyber attackers and their methods and tactics disclosed on the Internet, and automatically generates profiles based on this information. Cyber-attack information can be visualized by matching the automatically generated profiles with a wide variety of logs accessing the KDDI network.
Going forward, our monitoring system will be equipped with functions to predict attacks by analyzing various logs and to detect suspicious accesses at an early stage. In this way, we will further enhance our security monitoring using DX and AI in order to respond immediately when signs of any attack are detected.
Visualization of cyber attack information
Research and Development of Security Technologies by Digital Twin
The KDDI Group is engaged in various research and development efforts to realize a safe and secure digital society.
Particularly, KDDI Research, Inc. will contribute to ensuring safety and reliability in a society where cyberspace and physical space are integrated as a feature of the Beyond 5G era.
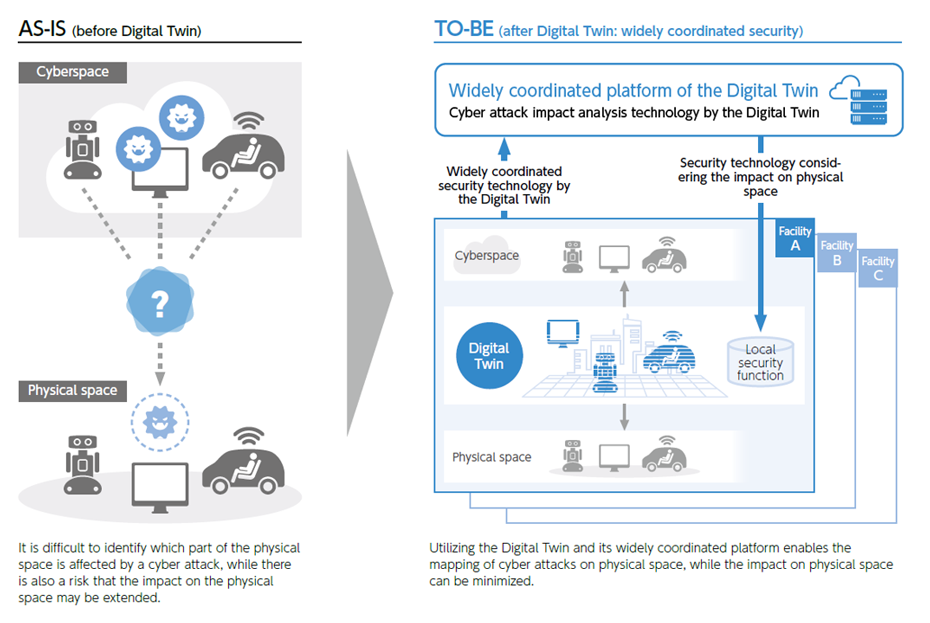
As the integration of cyberspace and physical space progresses in the Beyond 5G era, there is a risk that the actual damage to physical space will be enormous as the impact range of cyberattacks expands. Especially, in a world where IoT is integrated into society as part of critical infrastructure, a cyber attack on the IoT could have a significant impact on our lives.
To accurately grasp the scope of impact in both cyberspace and physical space, it is important to manage information in cyberspace, such as the IP address of the target of a cyber attack, and information in physical space in a form that links them together. Furthermore, it is necessary to understand and analyze the management units in a cross-sectional and extensive manner.
After collecting and analyzing threat information, which can have a significant impact on the physical space too, we will extensively provide threat information for the Digital Twin. In this way, we will build a platform for various Digital Twins to effectively implement security measures, at the same time as conducting demonstration experiments on actual cyberphysical systems in the future.
■Research and development items
- 1Widely coordinated security technology by the Digital Twin
- 2Cyber attack impact analysis technology by the Digital Twin
- 3Security technology considering the impact on physical space
Coordinated security platform between cyberspace and physical space by Digital Twin
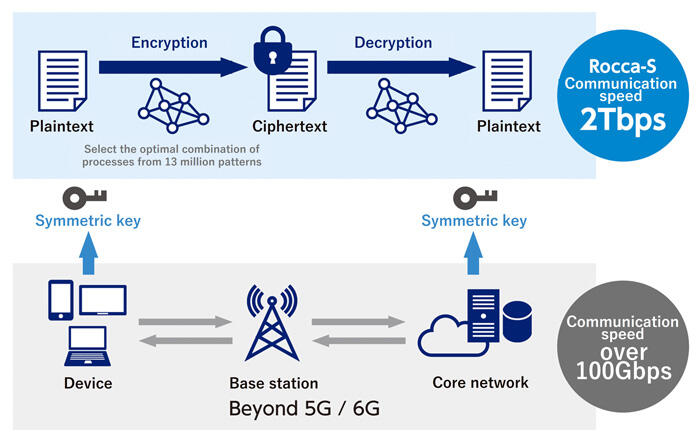
Ultra-high-speed common key encryption algorithm "Rocca-S" achieves the world's fastest processing performance of 2Tbps
Beyond 5G/6G research and development is underway with the goal of achieving communication speeds of over 100Gbps, and symmetric key cryptography is required to have processing performance equivalent to or higher than the communication speed of Beyond 5G/6G. In addition, to safely implement next-generation services, highly secure cryptographic algorithms that are resistant to quantum computers are required. "Rocca-S" is a cryptographic algorithm that meets these two requirements.
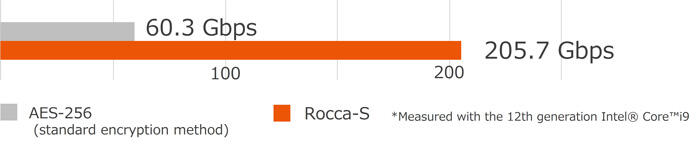
This time, we have optimized the processing per circuit scale through parallelization through hardware implementation, and achieved processing performance of 2Tbps, which significantly exceeds the communication speed targeted for Beyond 5G/6G. This increases the possibility of application to Beyond 5G/6G core networks, which require even higher speeds than wireless networks. In the future, we aim to popularize "Rocca-S".
This research is part of the results of the Ministry of Internal Affairs and Communications' "Research and Development on New Generation Cryptographic Technology for Secure Wireless Communication Services," commissioned by the Ministry of Internal Affairs and Communications under its "Research and Development for Expanding Radio Wave Resources (JPJ000254)."
Rocca-S encrypted communication in Beyond 5G/6G environment
Comparison of processing speed between Rocca-S and standard encryption method
Number of Serious Information Security Incidents
KDDI works to strengthen its information security across the Group, making efforts to reduce information security risks.
- Society
-
- Respect for Human Rights
- Supply Chain Management
- DE&I (Diversity, Equity and Inclusion)
- Human Resources
- Community Cooperation (in Japanese only)
- Awareness Raising and Education
- Safer and More Resilient Connected World
- Cyber Security and Privacy Protection
- Responsibility for Products and Services
- Innovation Management
- Customer Relationship Management
- Brand Management
- Initiatives outside Japan
- Stakeholder Engagement
- ESG Data (Social)
- Recommended Contents
-


